Can Cybersecurity use Generative AI?
Cybersecurity is going to be an issue that organizations of every type and size will just have to handle by the proverbial horns. Attackers and threats are in a constant tug-of-war with organizations over how defenses can break. Ideally, with how Generative AI can recreate its ow version of provided data, it should be able to train and adapt using an organization’s past cybersecurity incidents to better prepare for potential future threats.
Let’s securely build your cloud infrastructure, together
How Can Generative AI Find Use?
Early Threat Detection
Challenge:
Cyber threats are dynamic, evolving entities that can bypass traditional rule-based detection systems. Intruders constantly inspect entry points into a network for potential loopholes to exploit. Cybersecurity teams do the same, though it’s hard to predict how infiltrators might try to turn existing security measures in their favor. However, unusual patterns or behaviors indicative of cyber threats are often challenging to detect in real-time.
Sifting through inbound traffic can be overwhelming. Threats in a crowd won’t easily present who could be a potential attacker. By the time security teams could have searched half the potential vectors, the real attackers may have already made their move.
Solution:
Generative AI models, such as Generative Adversarial Networks (GANs), can analyze vast datasets to understand normal network behavior. These models are designed to take in vast amounts of data and put out something that imitates to the best of its capabilities, meaning it excels at learning patterns and can be employed to predict normal system behavior. Using past incident data, the model generates its own realistic synthetic data to identify subtle anomalies that may indicate potential threats. The model then applies what it’s learned to finding anomalies in a public network.
Implementation:
- Train GANs on historical network data to learn normal patterns.
- Train Generative AI models on diverse datasets representing normal system behavior.
- Use the trained model to generate synthetic data that represents normal behavior.
- Compare real-time data with the synthetic data representing potential infiltrators to identify deviations and potential threats.
- Continuously analyze incoming data to predict expected patterns.
- Identify anomalies by flagging deviations from the predicted behavior.
Automated Security Protocol Generation
Challenge:
Developing and updating security protocols manually is time-consuming and may leave vulnerabilities unaddressed. The main challenge is what needs to be continuously developed and when updates need to be implemented before existing security measures devolve into potential vulnerabilities.
Solution:
Generative AI can automate the generation of security protocols by analyzing historical threat data, current vulnerabilities, and industry best practices. Especially for organizations that handle multiple customers or clients’ data, remaining compliant is important.
Implementation:
- Utilize Generative AI to analyze historical threat data and identify common attack patterns. This can be done with the organization’s internal data or data from competitors within the same industry or field.
- Incorporate current threat intelligence and vulnerability assessments into the model.
- Generate dynamic security protocols that adapt to emerging threats in real time, providing the most simple plan for security maintenance possible.
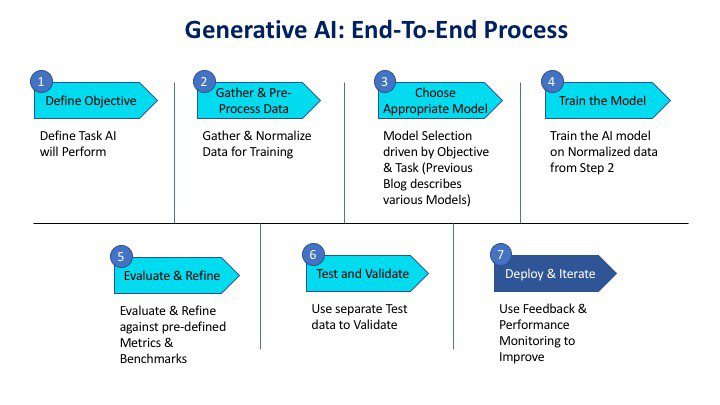
Natural Language Processing and New Security Policies
Challenge:
Interpreting and implementing complex security policies can be a manual and error-prone process. Writing down standard procedures is one issue, but making sure policies are followed needs to be verified thoroughly and consistently. Additionally, as cybersecurity does affect an organization as a whole, every sector should pitch in regarding changes to security policies. Practically, not everyone understands the inner workings of an organization’s security.
Solution:
Generative AI, particularly Natural Language Processing (NLP) models, can comprehend and generate security policies based on natural language inputs, making it easier for developers to implement and adhere to security measures.
Implementation:
- Train NLP models on security policies and guidelines.
- Develop a system that allows developers to input security requirements in natural language.
- Generate machine-readable security policies for implementation.
Behavioral Biometrics for Credentials
Challenge:
A common means of infiltration attackers might use is the impersonation of trusted staff and users to gain access to a network. This is accomplished either from stolen credentials or a hijacked account that the attacker now puppets. Traditional authentication methods may be susceptible to impersonation or unauthorized access and these types of attacks need to be carefully guarded against.
Solution:
Generative AI can enhance authentication by analyzing behavioral biometrics, such as typing patterns or mouse movements. A model can collect these various data points to create unique user profiles based on all members of an organization.
Implementation:
- Train models on user behavior data to create individual biometric profiles.
- Continuously analyze user behavior to ensure consistency with the established profiles.
- Use Generative AI to adapt authentication measures based on evolving user behavior.
Data Experts
AllCode is an AWS partner and has extensive experience working with datasets small, medium, and large. Get in touch with us and learn how we can help you leverage data to make better business decisions.
How Security can Benefit
1. Adaptive Defense Mechanisms:
Generative AI enables the creation of adaptive defense mechanisms that evolve with emerging threats, providing a proactive approach to cybersecurity.
2. Early Threat Detection:
By identifying subtle anomalies, Generative AI can point out potential threats long before they can make an impact, minimizing the impact of cyberattacks to begin with.
3. Efficient Resource Utilization:
Automated security protocol generation ensures that resources are allocated efficiently, addressing vulnerabilities based on real-time threat intelligence.
4. Human-Centric Security:
Natural Language Processing makes security policies more accessible, allowing developers and stakeholders to contribute to and understand security measures effectively.
5. Enhanced Authentication:
Behavioral biometrics add an additional layer of security, making it more challenging for attackers to compromise authentication systems.
The AI-Driven Future of Cybersecurity
Generative AI is reshaping the landscape of cybersecurity by introducing intelligent, adaptive, and anticipatory measures. Developers leveraging Generative AI for threat detection, anomaly detection, and security protocol generation are at the forefront of a new era in cybersecurity—a future where systems not only defend against known threats but also adapt in real-time to thwart emerging challenges. As cyber threats evolve, the synergy between Generative AI and cybersecurity becomes increasingly crucial in fortifying our digital ecosystems.
