How To
A comprehensive list of our how-to tutorials. Check out our step-by-step guides on how to solve a variety of common technical problems.
Creating A New AWS EC2 Key For A Third Party Developer
This guide will take you through the steps to create a new Key and then add it to your EC2 instance.
Read more ➞
Creating An IAM User For Third Party Developers
Allow secure tailored access to your AWS infrastructure to engineers and developers.
AWS Business Continuity Plan
Learn how to create an effective business continuity plan for your AWS stack.
Browse our How To Articles
Generative AI in Application Development
In the ever-evolving landscape of application development, Generative AI has emerged as a powerful force, revolutionizing how developers approach creativity, innovation, and problem-solving. People have already explored the technological potential in the realms of content creation such as video, auditory, text, and image generation. What isn’t discussed nearly as frequently is how developers can seamlessly integrate this technology to unlock new realms of possibilities in projects and applications they build.
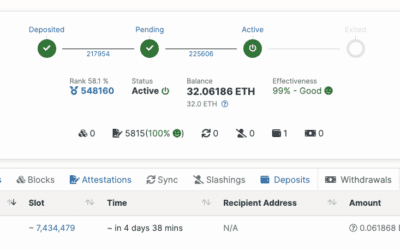
How do I withdraw rewards from Ethereum Staking on a Mac OS?
Step by Step tutorial on how to withdraw rewards from Ethereum staking on a Mac OS.
Developing an AWS Multi-Account Strategy
There are several good strategic reasons for having multiple accounts tethered to a single AWS environment. For security, governance, and scalability purposes, it is ideal to have a number of accounts working together in an environment for the various employees to have access. Ideally, the following should be incorporated into the environment to make the most of what AWS can offer.
GoDaddy to AWS Migration Guide
If you are looking for a useful guide on how to migrate your DNS from GoDaddy to AWS Route53, then you have come to the right place.
5 Types of Cybersecurity You Will Need
Cybercrime is a perpetually evolving threat that demands the most out of companies’ ability to adapt in turn. There are a variety of threats present that can damage a company in a variety of ways from siphoning critical information off to unwanted third parties to damaging company equipment or putting information behind a paywall. Even for those who aren’t security specialists, having a basic grasp of these concepts is important to have.
Using Stable-Diffusion and Dreambooth to create personalized AI art – Part 2 of 3
DreamBooth is a deep learning generation model used to fine-tune existing text-to-image models, developed by researchers from Google Research and Boston University in 2022. Originally developed using Google's own Imagen text-to-image model, DreamBooth implementations can be applied to other text-to-image models, where it can allow the model to generate more fine-tuned and personalised outputs after training on three to five images of a subject.
Using Stable Diffusion to create personalized AI art – Part 1 of 3
Using Stable Diffusion to create personalized AI art is possible; However, it takes a little bit of work. Stable Diffusion is an open-source text-to-image AI model that can generate amazing images from given texts in seconds. This first article will help you get the default Stable Diffusion installed on your local machine and check that it can run.
How to Create and Add a Slack Workspace
Slack is a business-oriented instant messaging platform that facilitates the sharing of relevant information among team members. Slack improves workplace communication by fostering collaboration across departments.
Creating a Robust Data-Driven Platform
Gathering data and applying it towards business operations is going to be critical going forward. Plenty of companies have already caught onto that trend and have put forward their own spins on data streamlining services that lets users seamlessly gather data from various streams securely and combine it into various spreadsheets and UIs in a way that minimizes risk, is cost effective, and lets users innovate faster. The following tools power some of the best power your web applications.
How-to Give AWS Route 53 IAM access
Our how-to guides cover various topics in detail. Learn what you need to with AllCode.