AWS CloudFormation Templates
AWS CloudFormation is designed to help users procure new AWS resources faster and more efficiently.
What is CloudFormation?
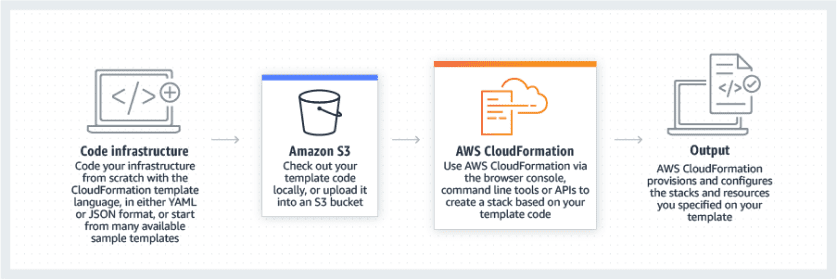
AWS CloudFormation aims to simplify the provisioning process and helps users update software on the users’ schedule. This can be easily conducted through a text file or one of the default templates AWS provides. Resources can be managed or created individually or tethered together as a stack.
CloudFormation templates are JSON or YAML formatted text files used as blueprints for building AWS resources. These templates automate behaviors needed for maintaining best practice actions and are widely applicable to DevOps. During stack update failures, CloudFormation ensures that the stack automatically rolls back to the previous known working state. Conditions help to establish certain circumstances under which new AWS resources are procured. The logs generated during the process can assist users in understanding the specific issue that led to the failure.
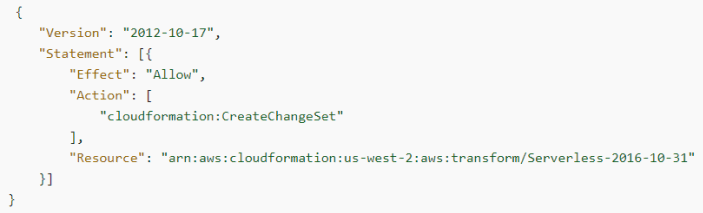
Additionally, the concept of a stack is elaborated as managing related resources as a single unit, all defined by the stack’s CloudFormation template. This allows for cohesive management and deployment of resources. Before updating a stack, you can generate a change set, which is essentially a summary of your proposed changes. Change sets allow you to preview how your changes might impact your running resources, especially critical ones, before you implement these changes.

We’re a Certified AWS Partner!
As an AWS Partner, AllCode is well-equipped to help its clients integrate CloudFormation templates into their applications, providing them with a reliable and scalable solution for real-time communication.
Why use AWS CloudFormation?
CloudFormation Change Sets are a feature that allows you to review potential updates to your stack before they are applied. When you want to make changes to your stack, creating a change set first allows you to assess these modifications’ effects on your deployed resources. Essentially, this tool generates a detailed summary of the proposed changes, giving you a clear preview. Additionally, it provides rollback protection during stack creation and update operations. If the creation of a stack fails, CloudFormation will automatically roll back changes made to the stack. By default, everything will be deleted in the event of a creation failure, ensuring that the stack remains in its original state. Users also have the option to disable rollback, which can be useful for troubleshooting failures.
During stack update failures, CloudFormation ensures that the stack automatically rolls back to the previous known working state. This mechanism prevents any partial or incomplete resources from being left behind and maintains the stack’s integrity. The logs generated during the process can assist users in understanding the specific issue that led to the failure.
- New templates can be created using JSON or YAML files. There are no advantages from using one format over the other.
- AWS CloudFormation templates are used to automate behaviors needed for maintaining best practice actions and are widely applicable to DevOps. Additionally, developers can audit alternatives to automate deployments.
- CloudFormation is better for scaling global infrastructure, regardless of where it is in the organization.
- Templates are surprisingly compatible with third-party and private resources, whether it be management, provisioning, or modeling resources. They even have circles of GitHub communities with projects that can be shared safely and systematically.

Download list of all AWS Services PDF
Download our free PDF list of all AWS services. In this list, you will get all of the AWS services in a PDF file that contains descriptions and links on how to get started.
How to use Templates
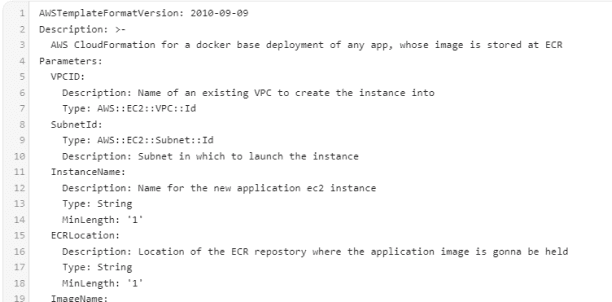
The primary objective is not to automatically procure resources as it is to automate how certain resources are set up with variables such as type, name, version, and security protocols for either inbound or outbound traffic established. As previously mentioned, a JSON or YAML file will consist of all the resources compiled in a stack with full details on each, including version number, type, and security protocols for inbound and outbound traffic.

AWS Service Business Continuity Plan
Download Free
- Variables can be selected individually to avoid having to manually hard code them.
- All resources will need to be declared, whether they are an S3 bucket or an EC2 instance. Each resource will have multiple properties tied to it, each of which can have subproperties related to it.
- The template must also declare any output variables that need to be imported into other stacks.
- Not all variables need to be chosen to deploy. Variables can be declared as needed.
- To avoid issues with regional-dependent variables, mapping will set conditions for selected variables that need to be in specific AWS Regions.
- To make establishing variables easier, AWS does have a complete library of variables and other references to help make compiling templates easier.
- Users can update the properties for resources in existing stacks. These changes can range from simple configuration changes, such as updating the alarm threshold on a CloudWatch alarm, to more complex changes, such as updating the Amazon Machine Image (AMI) running on an Amazon EC2 instance. Many of the AWS resources in a template can be updated, and we continue to add support for more.
- Conditions help establish certain circumstances under which new AWS resources are procured. For example, users might want to differentiate using a template when deploying to a production or test environment.
- Building on the template’s declarative language, the Transform section declares any macros the template will use. These macros will then execute in the specified order, so be mindful of how they are listed.
To further enhance the efficiency of managing multiple stacks, you can export a stack’s output values, allowing other stacks within the same AWS account and region to import these values. This facilitates seamless information sharing between stacks, which is essential for maintaining consistency and efficiency in large-scale deployments. Additionally, the resource import feature can be utilized for resources created outside of the CloudFormation environment. The capability to move resources between stacks by implementing a Retain deletion policy allows for greater flexibility and control over resource lifecycle management. Stack nesting and the creation of specialized stacks, such as those for Microsoft Windows, are also supported, providing structured and scalable options for complex infrastructure setups.
Integrating Security Features
Security will be another concern. With AWS’s shared security responsibility policies, developers are responsible for specifying which inbound or outbound content should be screened. In addition to fully using AWS’s other security tools, how traffic going in or out will be scrutinized will need to be specified with the other variables.
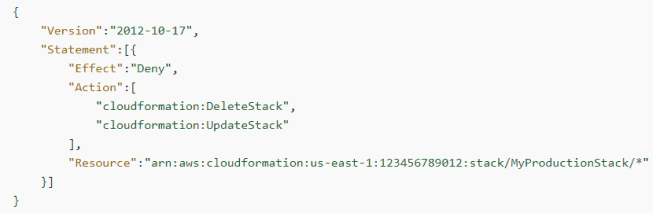
IAM can be utilized with AWS CloudFormation to effectively manage authorization and access control within an AWS environment. By using IAM with CloudFormation, administrators can specify and enforce what actions different users or roles can perform in relation to CloudFormation activities.
With IAM policies, administrators can define which users have the authorization to carry out specific tasks related to CloudFormation—such as viewing stack templates, creating new stacks, or deleting existing stacks. Moreover, administrators can further refine access by specifying what AWS services and resources are accessible to each user. This level of control ensures that users can only interact with resources that have been explicitly granted to them, thus enhancing security and compliance measures within the AWS environment.
- Under no circumstances should users have sensitive data in any of the variable categories, such as names. Worse, embedding credentials into the templates by default. If necessary, use a dynamic reference instead.
- By its default, CloudFormation will encrypt data at rest, while it’s in transit, and while it is within the environment network. However, customers are still responsible for setting encryption and storage policies.
- There are options to validate templates before using them to ensure dependencies and syntax errors don’t occur before the template is used to create any AWS resources.
Conclusion
Templates are incredibly useful for setting up new AWS resources and environments with less effort on the developer’s part. Setting up resources involves extensive variable configuration and setup before it can properly launch. Better yet, templates can be repeatedly reused or shared within an organization with sufficient leeway in how those templates are utilized.
Text AWS to (415) 223-9212
Text us and join the 700+ developers that have chosen to opt-in to receive the latest AWS insights directly to their phone. Don’t worry, we’ll only text you 1-2 times a month and won’t send you any promotional campaigns - just great content!
Our Case Studies
We explore how our team transformed a client’s challenge into a successful solution. By leveraging our expertise in software development and project management, we streamlined their operations, reduced costs, and accelerated time-to-market.


