Performing Vulnerability Scanning with AWS Inspector on AWS EC2, ECS, and Lambda
Introduction
AWS Inspector is a powerful security assessment service that helps you identify security vulnerabilities and compliance issues in your AWS resources. This document will guide you using AWS Inspector to scan vulnerabilities on three key AWS services: EC2 instances, ECS clusters, and Lambda functions.
Key Benefits
- Automated Service:
AWS Inspector automates the security assessment process, allowing it to function without human intervention. This ensures continuous and consistent security checks, significantly reducing the risk of human error.
- Regular Security Monitoring:
The service identifies security vulnerabilities and deviations from best practices before deployment and during production. This ongoing monitoring helps maintain a secure environment, giving you peace of mind that your AWS-hosted applications are protected.
- Leverage AWS Security Expertise:
AWS Inspector includes a comprehensive knowledge base of security rules and best practices regularly updated by AWS. You benefit from the latest security innovations and standards without manually updating your systems.
- Integrate Security into DevOps:
AWS Inspector integrates seamlessly into your existing DevOps processes as an API-bound service. It uses an optional agent for deeper visibility into EC2 instances, making it easy to incorporate security assessments into your development workflow. This empowers both development and operations teams to make security assessments a natural part of the deployment process.
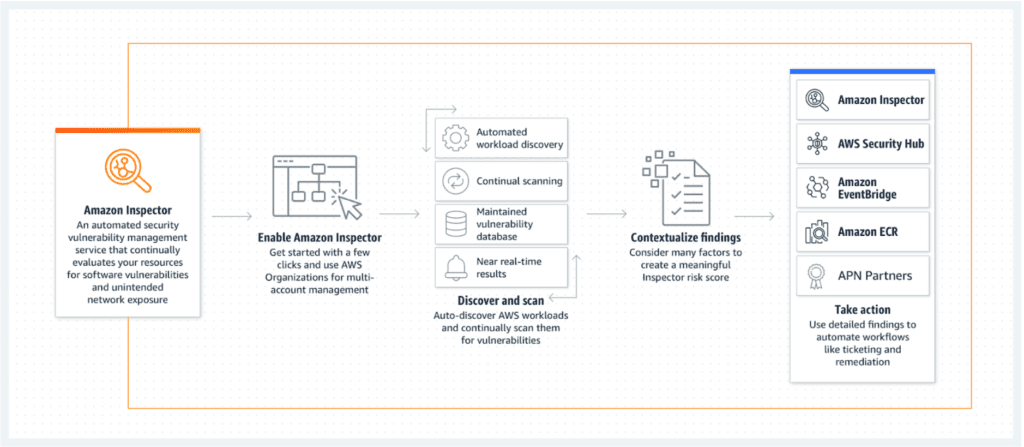
How it Works
Amazon Inspector conducts thorough automatic assessments of your AWS environment and generates a detailed findings report with actionable steps to enhance your security. Here’s a step-by-step breakdown of the process:
- Define Your Environment: Start by outlining the collection of AWS services and resources for your application. This scope ensures that every relevant component is included in the assessment.
- Set Assessment Duration: You can customize the length of the assessment, with options ranging from 15 minutes to 12 hours, or even up to a full day.
- Deploy Inspector Agents: These agents are installed on your EC2 instances and continuously monitor network traffic, file system activities, and running processes.
- Data Collection: The agents gather critical data on your system’s operations, which is then sent back to the Amazon Inspector for analysis.
- Security and Compliance Comparison: The collected data is evaluated against predefined security rules and compliance benchmarks to identify potential vulnerabilities and issues.
- Generate Findings Report: Finally, Amazon Inspector compiles its findings into a comprehensive report detailing any discovered security threats and providing actionable recommendations for mitigation.
Prerequisites
Before you begin, ensure that you have the following prerequisites in place:
- AWS Account: You should have an active AWS account with appropriate permissions to access AWS Inspector.
- Inspector Agent (for EC2): For EC2 instances, you may need to install the AWS Inspector Agent on the instances running your applications. This agent collects data about your instances and sends it to the Inspector for analysis. However, this is not required for ECS or Lambda.
Steps to Perform Vulnerability Scanning
EC2 Instances
- Create an Assessment Target:
- Log in to the AWS Management Console.
- Navigate to AWS Inspector and select “Assessment targets.”
- Click “Create assessment target” and select “EC2 instances.”
- Choose the EC2 instances you want to assess.
- Create an Assessment Template:
- In the AWS Inspector console, go to “Assessment templates.”
- Click “Create assessment template” and select “Security findings.”
- Choose the assessment target created in the previous step.
- Configure the assessment template with your desired rules packages and duration.
- Start an Assessment Run:
- Go to “Assessment runs” in the AWS Inspector console.
- Click “Start an assessment run” and select the assessment template created earlier.
- Review and confirm the settings, then start the assessment run.
- Review Assessment Findings:
- Wait for the assessment run to complete.
- Once finished, view the findings in the Inspector console.
- Address and remediate the identified vulnerabilities in your EC2 instances.
ECS Clusters
- Create an Assessment Target:
- In the AWS Inspector console, select “Assessment targets.”
- Click “Create assessment target” and select “ECS clusters.”
- Specify the ECS cluster you want to assess.
- Create an Assessment Template:
- Navigate to “Assessment templates.”
- Click “Create assessment template” and select “Security findings.”
- Choose the assessment target created in the previous step.
- Configure the assessment template with your preferred rules packages and duration.
- Start an Assessment Run:
- Access “Assessment runs” in the AWS Inspector console.
- Click “Start an assessment run” and pick the assessment template from step 2.
- Confirm the settings and launch the assessment run.
- Review Assessment Findings:
- Monitor the assessment run status until it is completed.
- Examine the assessment findings in the Inspector console.
- Take necessary actions to mitigate any security issues discovered in your ECS cluster.
Lambda Functions
- Create an Assessment Target:
- In the AWS Inspector console, select “Assessment targets.”
- Click “Create assessment target” and select “Lambda functions.”
- Specify the Lambda functions you want to assess.
- Create an Assessment Template:
- Navigate to “Assessment templates.”
- Click “Create assessment template” and select “Security findings.”
- Choose the assessment target created in the previous step.
- Configure the assessment template with your desired rules packages and duration.
- Start an Assessment Run:
- Visit “Assessment runs” in the AWS Inspector console.
- Click “Start an assessment run” and pick the assessment template from step 2.
- Confirm the settings and launch the assessment run.
- Review Assessment Findings:
- Wait for the assessment run to conclude.
- Access the Inspector console to review the findings.
- Act on the identified vulnerabilities to secure your Lambda functions.
What about managed database services like RDS and Elasticache?
As of September 2021, AWS does not allow direct vulnerability scanning of RDS (Relational Database Service) instances using AWS Inspector or other vulnerability scanning tools. AWS RDS is a managed database service, and the underlying infrastructure and security configurations are managed by AWS, limiting the ability for customers to perform traditional vulnerability scanning on these instances.
However, AWS provides security features and recommendations to help secure your RDS instances, including network security through Amazon VPCs, encryption at rest and in transit, and database-specific security features such as authentication and authorization.
To ensure the security of your RDS instances, consider the following best practices:
- VPC Security Groups and Network Access Control Lists (NACLs): Configure security groups and network ACLs to control inbound and outbound network traffic to your RDS instances.
- Encryption: Enable encryption at rest and in transit for your RDS instances to protect data both at rest and during transmission.
- Authentication and Authorization: Implement strong authentication and authorization mechanisms to control who can access your RDS databases and what actions they can perform.
- Parameter Groups: Use parameter groups to fine-tune database engine settings to meet your security and performance requirements.
- Database Auditing: Enable database auditing features to monitor and log database activities for security and compliance purposes.
- AWS Identity and Access Management (IAM): Use IAM to manage access to AWS resources, including RDS, by creating IAM database authentication.
- Regular Backup and Patching: Regularly back up your databases and apply database engine patches and updates to address security vulnerabilities.
