What is Calico?
Calico is a network and network security solution for containers, virtual machines, and native host-based workloads that is available as an open source project. In addition to Kubernetes, OpenShift, Mirantis Kubernetes Engine (MKE), OpenStack, and bare metal services, Calico also supports a wide range of other platforms and technologies. Utilizing Kubernetes pod selectors and labels, you can use Calico network policy enforcement to implement network segmentation and tenant isolation on your EKS environment. For EKS clusters, this is useful when implementing a zero-trust network architecture, in which network traffic must be expressly permitted to reach workloads.
AWS + TIGERA
Using AWS and Tigera’s Kubernetes-native networking, security, and observability services, DevOps engineers, system administrators, and platform owners can deploy cloud-native apps in their EKS and AWS self-managed Kubernetes settings with minimal effort. Users can create their apps using AWS services while also addressing their networking and security requirements using Calico.
Bottlerocket is also supported by Calico on Amazon Elastic Kubernetes Service (Amazon EKS). Amazon created Bottlerocket, an open source Linux system, to run containers focused on security, operations, and manageability at scale. It is one of the first EKS-optimized operating systems to have eBPF support in the Linux kernel. Calico can extend this foundation to improve the base networking for EKS beyond simply adding network policy support, such as accelerating network performance, eliminating the need to run kube-proxy, and preserving client source IP addresses when accessing Kubernetes Services from outside the cluster.
Maintaining the integrity of EKS clusters
When it comes to embracing containers and Kubernetes, security is a major problem. Due to security concerns, a large number of enterprises have faced security issues or have delayed the deployment of Kubernetes applications into production as a result of security concerns. It works on top of open-source Calico to provide additional features and capabilities to secure your EKS clusters and certify compliance with various security standards. Calico Enterprise is available as a subscription service.
- RBAC-based policy administration
- Detection of network attacks
- A Policy for DNS and the Application Layer
- Compliance reports
- firewall integration
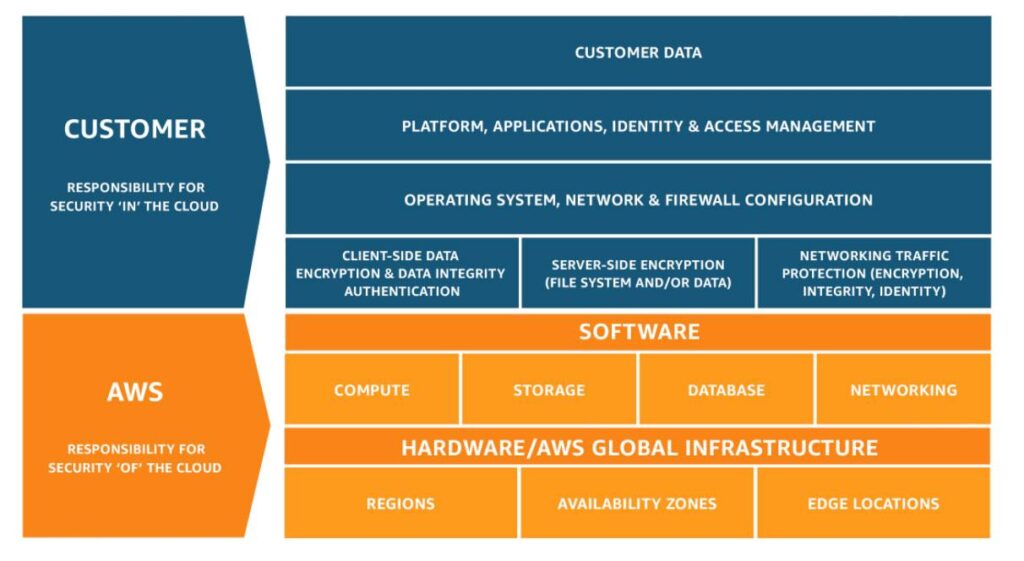
AWS and the customer share responsibilities for security and compliance.
The following is the shared responsibility Model:
It is possible to design, monitor and troubleshoot EKS segmentation and access control rules using cloud-native tools that may be incorporated into the CI/CD pipeline with the help of these features.
Network intrusion detection identifies malicious network activity occurring both within and outside of the EKS cluster and alerts the administrator.
Troubleshooting and Visualization of Networks
Troubleshooting connectivity difficulties across microservices can be incredibly time-consuming and frustrating. It is frequently necessary to work together with multiple teams in order to identify and resolve the problem. When a connectivity issue occurs between your microservices operating on Kubernetes clusters, Calico Enterprise provides tools to quickly identify and remedy the cause of the problem. Calico Enterprise also provides capabilities to identify and resolve possible connectivity issues before they occur. Attempts to connect microservices in Calico Enterprise are logged, as are the performance metrics associated with such connections. Included in this category are DNS logs and L7 metrics such as HTTP request codes as well as the length of each request.
Each log entry contains important Kubernetes metadata, such as
- The source and destination namespaces, as well as the time of day.
- A set of labels and pods for the source and the destination.
- What policy evaluated the link, whether it was accepted or rejected, and why it was accepted or denied are all important questions.
Using Calico Enterprises, you can view and engage with a live, interactive depiction of the microservices connections within the EKS cluster called a Service Graph. This tool highlights approved and disallowed flows, displays alarms on any issues, and allows users to drill down into the details of each flow for the purpose of troubleshooting. A packet capture can also be started directly from the graph in order to obtain more precise network information.
Calico Cloud enables developers and administrators who wish to implement security policies on (EKS) or Amazon Elastic Compute Cloud clusters to get up and running in a matter of minutes with little configuration. When it comes to containers with Kubernetes, Calico Cloud delivers a comprehensive networking and security policy architecture that aids in the security of communications by managing traffic flows.
EKS includes built-in support for Calico, which allows it to provide a robust implementation of the entire Kubernetes Network Policy API without the need for other dependencies. Users of EKS who want to go beyond the capabilities of the Kubernetes network policy API can make full use of the Calico Network Policy API.
Additionally, you may utilize Calico for networking on EKS in place of the default AWS VPC networking, which eliminates the need to use IP addresses from the underlying virtual private cloud. Calico’s networking features, including its flexible IP address management capabilities, are fully accessible as a result of this configuration.
Installation
You can install Calico by following the same steps as you would for Helm or manifests. Due to the fact that the manifests are not updated by Amazon EKS, we propose that you utilize Helm instead, as the charts are maintained by Tigera.
When the new Tigera operator and Calico capability is released, Amazon EKS does not test and verify it on Amazon EKS clusters. If you have any problems with Calico during the installation or use of the software, please contact Tigera Operator and the Calico Project directly. Before installing any new Tigera operator or Calico version on your cluster, you should always check with Tigera to ensure that they are compatible with your existing cluster.
