Removing Needless Digging
Centralized Log Management (CLM) is a powerful system that offers a multitude of capabilities to streamline log data management and enhance overall operational efficiency. By automatically categorizing and consolidating all log data into a centralized server accessible through a unified user interface, CLM significantly reduces the time spent searching for scattered logs. The platform provides additional tools on the interface for seamless analysis and organization of data, effectively categorizing files by type and source.
Constant Monitoring and Logging
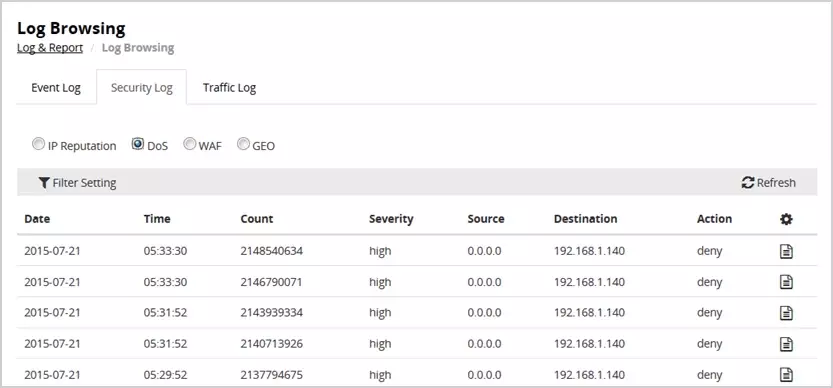
In addition to simplifying log organization, CLM excels in error tracking by monitoring IT environment activity and tracking essential metrics in real-time. Administrators can swiftly identify potential errors and suspicious activities, thanks to the system’s ability to set up event-based triggers for immediate alerts. Search results are intelligently arranged to display crucial information such as IP addresses, event names, timestamps, incident severity, and corresponding actions taken, facilitating efficient incident response.
CLM offers robust event logging functionalities that enable users to establish specific parameters for auditing unauthorized changes across various files and databases. The system’s alert system promptly notifies administrators of any unauthorized activity, allowing for timely intervention. By implementing tags to filter events, administrators can prioritize responses based on the severity of the identified issues.
Catching Invasive Activity
Centralized log management enhances security measures by providing in-depth insights into log contents, enabling proactive security actions. By aggregating logs from security devices and internal components, such as firewalls and endpoint protection services, CLM constructs a comprehensive narrative of security breaches, aiding in the identification of potential threats and attackers’ behaviors. This detailed logging mechanism offers valuable insights into system operations and supports preemptive security measures.
Compliance remains a critical aspect of cybersecurity, and CLM excels in facilitating regulatory adherence. With its robust capabilities for logging all system activities, CLM not only enables digital forensics analysis but also simplifies the compilation of compliance reports. The platform’s dashboard features default and customizable templates for generating audit reports, ensuring alignment with security standards like PCI DSS, HIPAA, and SOX.
AWS Centralized Logging
All data sources must first be integrated with the centralized server and a log management tool before logs can be collected. Integration can be done through either an agent on the source server or more native methods, depending on the environment type. For example, AWS conducts its own centralized log management through CloudWatch. Amazon’s CloudWatch deploys in the main account and is created in the regions where the service is present. Users can configure filters for group types on their way to being streamed to the centralized server. There is the option to generate template logs to test the flow to ensure that the data sourcing works. Amazon Kinesis Data Streams and Kinesis Data Firehose are provisioned to catalog and organize the collected data and deliver it to an Amazon OpenSearch Service domain where a Lambda function is invoked to turn the logs into a document. More details on CloudWatch can be found on AWS’ own website.
In Summary
Centralized log management is now a crucial element in understanding an application’s internal workings and learning what people are interested in or how to protect it. The internal functionality of a system is incredibly complex and the smallest details can easily become lost behind countless other mundane logs. The first step to resolving any issue is understanding how it happened in the first place. Then there’s learning how to prevent incoming threats to avoid incurring the costs of reparations and damage in the first place. As cybersecurity threats become a more common issue, meeting newer security standards will be evermore important. Having a centralized log management system can not only aid existing IT and security teams in their jobs but also ensures that a platform remains compliant with regulations.
