Share

AWS WAF
Why AWS WAF?
DDoS attacks are among the most common and disruptive forms of web attacks. Attackers flood web servers with bulk requests, causing applications to slow down and become inaccessible to genuine users. This not only impacts brand reputation but can also have serious implications for business operations.
Another critical threat is SQL injections, where attackers exploit vulnerabilities in SQL databases to run malicious queries on websites or applications. Without proper security measures, attackers can access confidential account and business information, posing a significant risk to data integrity.
If your web apps or APIs are at risk of being hacked or compromised by bots, AWS WAF (Web Application Firewall) is a virtual firewall that can assist defend you from these threats. AWS WAF gives you comprehensive control over traffic accessing your applications by allowing you to set security rules that restrict bot traffic and stop classic attack types like SQL injection and cross-site scripting.
Additionally, you have the option of creating rules that only allow certain types of traffic. Preconfigured rules for AWS WAF, administered by AWS or AWS cloud computing marketplace sellers, can be used to deal with security problems such as the OWASP Top 10 security risks and automated bots that utilize excessive resources, skew metrics, or cause downtime in AWS cloud systems. These recommendations are frequently revised to reflect any changes in the situation.
AWS WAF has a security rule system that allows you to automate the generation, deployment, and maintenance of safety rules. Your CDN solution, the Application Load Balancer for your web servers or origin servers on EC2, Amazon API Gateway for your REST APIs, and AWS AppSync for your GraphQL applications may all use AWS WAF on Amazon CloudFront. Amazon Web Services offers a CDN solution called Amazon CloudFront. Your application’s daily web request volume and the number of rules installed define how much AWS WAF costs, so there are no hidden fees.
How it Works
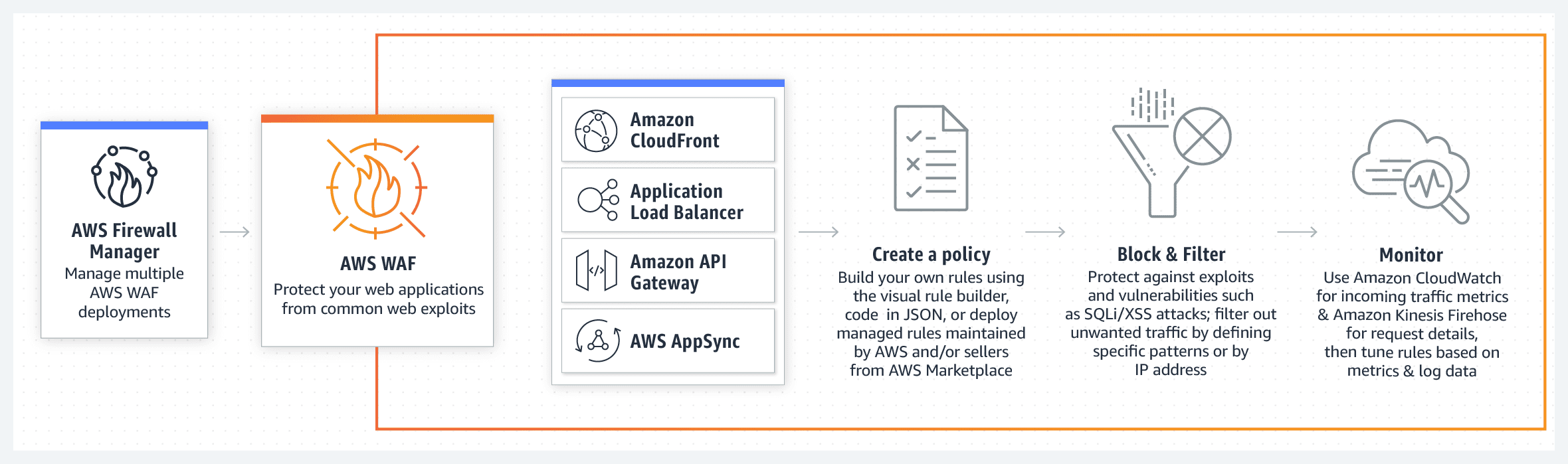
Image sourced from Amazon Web Services
Features
- Filtering of web traffic
AWS WAF’s web traffic filtering criteria include custom URIs and IP addresses. HTTP headers and body and HTTP headers and body are among the other criteria. This functionality serves as a second tier of defence against web attacks that try to exploit weaknesses in bespoke or third-party web applications. The AWS WAF also simplifies the process of enforcing rules to guard against common web vulnerabilities like SQL injection and cross-site scripting.
It is possible to apply rules to multiple websites at the same time using the AWS WAF. Rather of having to build new rules for every web application, you can construct a single set of security rules that can be applied to all of the websites and web applications in the environment.
- AWS WAF Bot Control
Managed rule groups in AWS WAF allow for visibility and control over bot activity that may consume excessive resources, distort data or create disruption. A few mouse clicks allow you to block or prevent common bots, such as crawler and scraper programmes or status monitors and search engine crawlers, from operating on your website. The Bot Control managed rule group, when used with other Managed Rules for WAF or custom WAF rules, can help secure your applications even further.
- Preventing account takeover fraud is important.
In the AWS WAF Fraud Control service, a financial fraud prevention managed rule team assesses your application’s login page for login attempts and user accounts using compromising credentials. By working with the government, it is possible to avoid credential stuffing attacks, conventional warfare login attempts, and any other suspicious login activity. With the optional JavaScript and iOS/Android SDKs, you may collect more information about user devices that attempt to connect into your application and use it to further protect your application against automated login attempts by bots. Controlled Rules for AWS DevOps includes a feature called Account Takeover Prevention, which may be used in combination with Bot Control to prevent bots from seizing over your account.
- Feature-length API
AWS WAF may be completely controlled via APIs. An organization’s competitive advantage comes from having the ability to standardise and integrate rules into the development and design process. For instance, a developer who is intimately familiar with the web application can create a security rule that would be applied to it before deployment. To prevent the need for complex handoffs between application and security teams to guarantee that rules are up to date, incorporate security into your development process.
CloudFormation sample templates allow you to describe all of the security rules you want to implement for your web applications provided over Amazon CloudFront, which can then be automatically generated and provisioned by AWS.
- Real-time visibility is essential.
Real-time data and raw requests can be collected using AWS WAF, including data about IP addresses and geographical areas as well as info about URIs, User-Agent, and Referrers. AWS WAF is linked with Amazon CloudWatch, making it possible to generate custom alarms when limits are exceeded or specific attacks occur, making it simple to observe and respond to attacks. As a result of this information, new rules can be developed that will better protect apps because of this information.
- Integration with Amazon Web Services Firewall Manager
Using a single AWS account, you can centrally manage multiple AWS WAF deployments with AWS Firewall Manager. In addition, new resources can be checked to see if they adhere to a defined set of security criteria. In the event of a policy violation on your network, Firewall Manager alerts your security team so they can respond promptly and take appropriate action.
Benefits
- Protection against web-based threats that are flexible
In less than a minute, AWS WAF rules may be propagated and updated across your whole environment, allowing you to quickly address security issues as they arise. Web application firewalls (WAFs) have hundreds of rules that can examine any part of a web request while imposing the least amount of latency on incoming data. AWS WAF protects web applications from attack by filtering traffic according to rules you specify. Everything from Proxy servers to HTTP protocols to the HTTP body and URI strings can be included in web request filtering. Typical attack patterns like SQL injection and cross-site scripting can no longer exploit your system as a result of this.
- Managed rules let you save time.
When you use Managed Rules for AWS WAF, your systems can be shielded from a range of common threats within minutes of deployment. These threats include OWASP’s Top 10 Security Risks, Content Management System (CMS) Threats, and vulnerabilities identified in developing Common Vulnerabilities and Exposures (CVEs). Additionally, the automatic updates of these controlled rules ensure that your defenses stay up-to-date without requiring manual intervention. By leveraging these pre-configured rules, you can focus more on developing your applications while ensuring robust security measures are in place.
- Enhancement in the amount of online traffic
With the near-real-time visibility provided by AWS WAF, Amazon CloudWatch can produce new rules or warnings based on your web traffic. Individual rules or the entire inbound traffic stream can be monitored with precise control over the metrics that are emitted. The whole header data of each evaluated web request is also captured for use in security automation, analytics, and audits with thorough logging.
- Implementation and maintenance are made simple.
If you’re using Amazon CloudFront as part of a CDN solution, the Application Load Balancer, Amazon API Gateway (for REST) or AWS AppSync (for GraphQL) as part of a cloud computing architecture, you can use AWS WAF to protect and secure your apps. The use of a reverse proxy, additional software or DNS configuration or SSL/TLS certificate management is not necessary. Neither is a reverse proxy required. By integrating AWS Firewall Manager, you can define and administer your rules from a single location while also reusing them across all web apps you need to protect.
- Easy-to-use bot monitoring and control, including blocking and rate-limiting
Amazon Web Services’ AWS WAF Bot Control service can help you monitor and control bot traffic that is aimed towards your apps and services. Typical bots like status monitors and search engines can be monitored using the AWS WAF panel. Insights regarding bot traffic, such as its category, identity, and other pertinent features, can be obtained precisely and in real-time. Setting a rate limit on traffic can also prohibit or limit traffic from common bots like scrapers, scanners, and crawlers. Additionally, the AWS Firewall Manager service can be used to implement the Bot Control controlled rule group across several clients in your AWS Organization.
- Applications should be constructed with security in mind from the start.
The AWS WAF API or the AWS Management Console can be used to configure all of the AWS WAF’s features. This gives your DevOps team the ability to implement rules that are specific to the applications they are building, thereby improving online security for your firm as a whole. As an additional benefit, this allows you to incorporate web security into the growth process chain at numerous points, from developers writing code to DevOps engineers deploying software to security administrators who enforce a set of rules across an entire organisation. This is a significant advantage.

Download list of all AWS Services PDF
Download our free PDF list of all AWS services. In this list, you will get all of the AWS services in a PDF file that contains descriptions and links on how to get started.
Use Cases
- With a firewall at the network’s edge, unwanted bot traffic can be blocked.
At the network’s edge, AWS WAF and CloudFront’s Bot Control collaborate to limit the traffic of malicious bots. By leveraging Bot Control in AWS WAF, you can effectively reduce operational and infrastructure costs associated with scrapers, scanners, and crawlers. Additionally, Bot Control plays a crucial role in eliminating deceptive bot traffic that could skew traffic and conversion metrics, ultimately enhancing the user experience.
- Ensure the safety of your proprietary information.
Crawlers and scrapers are tools that websites utilize to index their content, extract files from their APIs, or otherwise make unlawful use of these resources. Controlling individual bots or a group of bots, such as search engine crawlers and scrapers, can be done via Bot Control. Search engine web crawlers can’t be prevented since Bot Control can’t be turned off by default.
- Content that doesn’t appeal to bots should be created in response.
With WAF features like Bot Control and unique answers, you can tailor application operations for bot traffic and make them more user friendly. In terms of SEO, “scraping” bots may bring visitors to your site, but they may also cause your real-time pricing database to fail. To ensure that bots aren’t sent to out-of-date price pages, AWS WAF can direct them to a cached endpoint instead.
Need help on AWS?
AWS Partners, such as AllCode, are trusted and recommended by Amazon Web Services to help you deliver with confidence. AllCode employs the same mission-critical best practices and services that power Amazon’s monstrous ecommerce platform.
Pricing
This includes the amount of web access control lists (web Basic input / output system), the number of rules you apply to each one, as well as the volume of web requests. It’s not necessary to make any commitments right now. AWS WAF is not included in the prices of Amazon CloudFront, Application Load Balancer (ALB), Amazon API Gateway, and AWS AppSync. If you create several web ACLs or rules for multiple web ACLs, you will be paid separately. Depending on how many web requests the web ACL handles, more fees will be incurred. The pricing structure for AWS services is the same across all regions. Each hour of use is charged at a prorated monthly rate. Subscribing to a controlled rule group offered by an AWS Marketplace vendor will come at an additional cost. AWS WAF fees aren’t the only costs to consider.
Costs are determined by three main variables:
Number of Web ACLs: Each Web ACL (Web Access Control List) is priced at a flat rate of $5 per month. Customers will incur charges based on the quantity of Web ACLs they utilize.
Number of Rules: The pricing structure includes a charge of $1.00 for every rule implemented within a Web ACL on a per month basis. This cost factor is directly proportional to the number of rules configured by the customer.
Request Count: Customers will be charged at $0.60 per million web requests processed by the AWS WAF service. This component of the pricing model is based on the volume of incoming web traffic and requests handled by the Web Application Firewall.

Text AWS to (415) 890-6431
Text us and join the 700+ developers that have chosen to opt-in to receive the latest AWS insights directly to their phone. Don’t worry, we’ll only text you 1-2 times a month and won’t send you any promotional campaigns - just great content!
Related Articles
Building an AI-Powered Communication Hub
Your customers reach out through SMS. Through email. Through WhatsApp. Through web chat.
Your team responds through… spreadsheets? Disconnected inboxes? Maybe a CRM that sort of ties things together?
Meanwhile, each channel has its own queue, its own response time, its own tribal knowledge about how to handle common questions. Customer context gets lost between channels. Response quality varies wildly depending on who’s working.
There’s a better way. Amazon Bedrock—combined with AWS End User Messaging and SES—enables enterprises to build unified communication hubs where AI handles routine inquiries across every channel, escalates complex issues to humans, and maintains full context throughout the customer journey.
Automating Email Triage with Generative AI
Your team processes hundreds—maybe thousands—of emails per day. Each one needs to be read, understood, categorized, and routed to the right person.
That’s a lot of human brainpower spent on triage.
What if AI could handle that categorization in seconds? What if urgent emails automatically escalated, routine inquiries queued for batch processing, and spam silently filtered—all without human intervention?
AWS Introduces 224 New AWS Competency Partners
AWS welcomes 224 new certified partners in AI, cloud ops, security & more. Discover specialized expertise across industries. Partner with the best.