Consolidate an Account Hierarchy
After inviting all team members to the environment of choice, there will need to be an established structure of priority, permissions, and responsibilities for the various stages of development. This is to help accomplish two separate goals. Each role should be defined in its purpose and can help to keep accounts focussed on billing separate from development, testing, and production. The second is for security purposes and the need for compliance. With how an environment can be potentially infiltrated, it is important to have limited scopes to what each account can have access to. This process is called isolation.
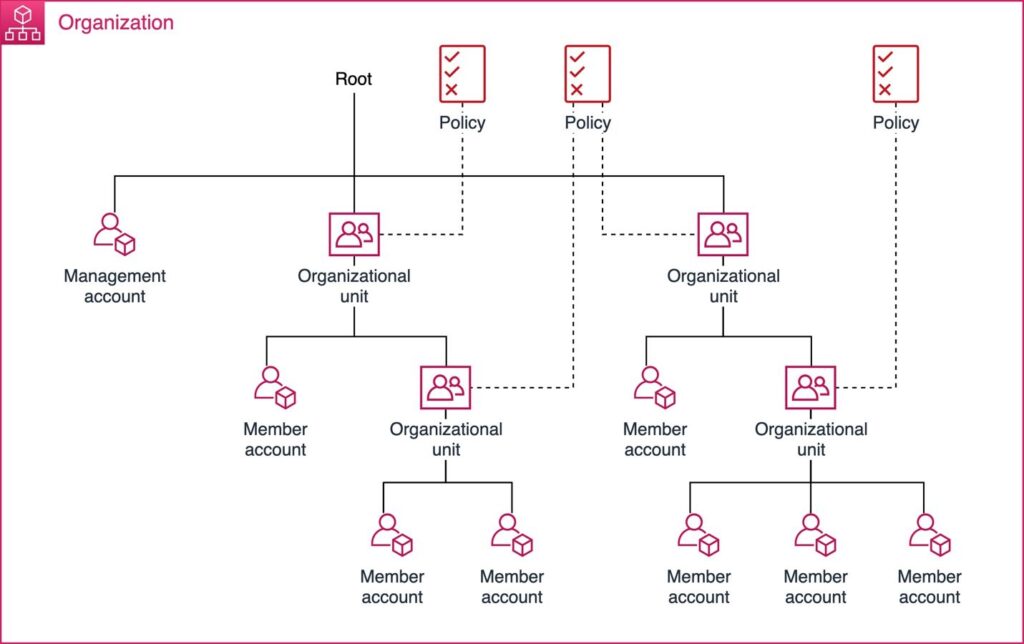
Finally, there’s the need for consolidation. Consolidation is the process of evaluating existing accounts to identify opportunities to reduce internal complexity. Merging multiple accounts that bear similar functionality or workloads helps minimize the number of accounts that need to be managed. It means overall fewer accounts to have to worry about. This can all be managed through AWS Identity and Access Management to better manage accounts internally. For more on bringing multiple AWS accounts into a single environment, have a look at our extensive guide here.
Internal Network Control
AWS has extensive control over the inner workings of an environment. This includes the Virtual Private Cloud (VPC), peering, transit, gateways, and AWS Direct Connect to provide customers with secure outlets for services without compromising the safety of the environment. Amazon also provides a number of in-house solutions for firewalls, security groups, and network access controls. Centrally, handled data can be managed through AWS Data Pipeline, AWS Glue, and AWS Lake Formation so central accounts can manage how data is processed across different accounts.
Security and compliance are big concerns for AWS environment. Because of how many of their clients are qualified to help in different industries including the public sector, handling information correctly and securely is a high priority. Along with the aforementioned account functionality and organization, other services on the AWS catalog that can help with security are AWS CloudTrail for centralized auditing, AWS Config for managing configurations and monitoring for compliance standards, and AWS Security Hub to put all security functions behind one single UI. Better yet, a good bulk of these more basic security functions can be fully automated to complete on their own to reduce time spent on maintenance.
Resource Acquisition
There are a variety of assets to handle from account to account required for environment operations. AWS operations can quickly become expensive and determining how much an organization can afford to spend on specific resources can be difficult to understand. For organizations interested in sharing resources when one account does not need them at a certain moment, AWS Resource Access Manager (RAM) and the AWS Service Catalog provide options to share resources and services. Because of how the Amazon Cloud works, new infrastructure can be acquired easily by utilizing infrastructure-as-code tools such as AWS Cloudformation and AWS CDK (Cloud Development Kit) to either procure new resources or manage existing ones. As environment development continues, CI/CD pipelines can be installed for more reliable deployments.
Then there are the cost management controls and the role they play in an environment. The billing controls AWS provides such as AWS Cost Explorer and AWS Budgets can easily tie expenditures and billing back to specific resources and the services that use them. Through careful analysis of an environment’s operations and what it can afford to cut back on, users can expect to see reduced expenses as development continues. How “optimal spending” is defined largely depends on the environment owners’ funding, what their business objectives are, and how expansive those operations need to be.
Continued Maintenance
If having multiple accounts on a single environment is going to continue being a crucial component of a company’s functions, the environment owner will need to constantly run maintenance and fully evaluate all of the services in use. For environments with multiple accounts running internally, there is great emphasis placed on giving accounts the right permissions and access to services and data. For more on the health of an AWS environment, we would recommend reviewing the Well-Architected Framework and the pillars it establishes.
