There are a number of different ways to implement AWS security monitoring.
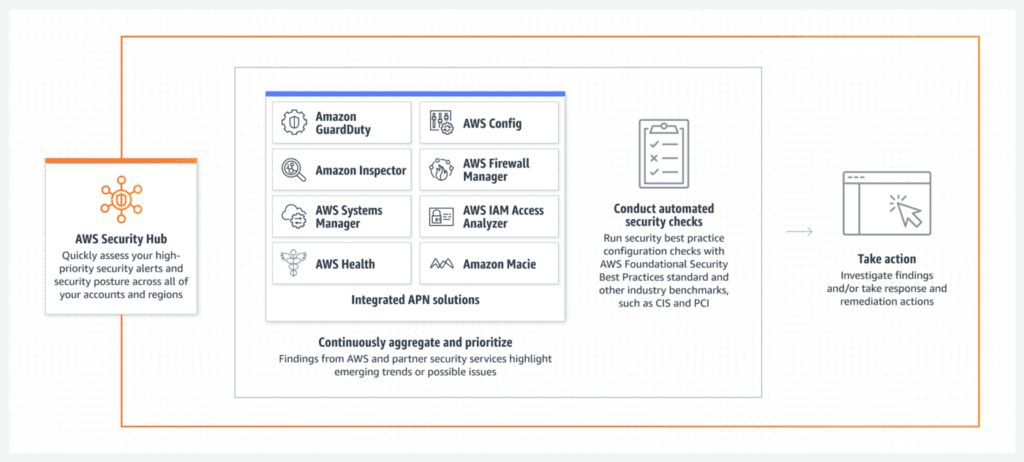
The AllCode recommended process is to:
- Configure AWS CloudTrail to track changes to your AWS resources and send logs to Amazon S3. This will give you a record of all API calls made to your AWS account, including changes made through the AWS Management Console, AWS SDKs, and command line tools.
- Set up Amazon CloudWatch to monitor your AWS resources and the applications that you run on AWS. CloudWatch can be used to collect and track metrics, collect and monitor log files, and set alarms.
- Use Amazon GuardDuty to detect and block malicious activity in your AWS accounts. GuardDuty uses machine learning and threat intelligence feeds to identify unusual activity, such as unexpected network traffic or access to sensitive data.
- Implement AWS Config to continuously monitor and record your AWS resource configurations. AWS Config can be used to audit changes to your resources and alert you when a resource is not compliant with your desired configuration.
- Use AWS Identity and Access Management (IAM) to manage access to your AWS resources. IAM enables you to create and manage users and groups, and control their access to resources by using policies.
- Consider implementing multi-factor authentication (MFA) for additional security. MFA requires users to provide an additional form of authentication, such as a code from a hardware token or a text message sent to a phone, before they are granted access to your resources.
- Regularly review your security measures and update them as needed to ensure that your AWS environment remains secure. This may include applying security patches, rotating credentials, and disabling unnecessary services.
To visualize GuardDuty data in AWS QuickSight, you can use the GuardDuty Findings as a data source. You would need to export the findings to an Amazon S3 bucket first, and then connect QuickSight to the S3 bucket as a data source. This way you can create visualizations and dashboards in QuickSight using the GuardDuty data, allowing you to analyze and understand the security state of your AWS environment.
Alternatively, you can use the integration between Amazon GuardDuty and AWS Security Hub which provides the ability to send findings to QuickSight and allows you to create visualizations and dashboards directly from the security findings.
It is important to note that in order to use this feature, you will need to have a QuickSight Enterprise edition, which allows you to access data stored in S3, as well as permissions to access the S3 bucket, where the findings are stored, and access to the appropriate security findings via GuardDuty or Security Hub.

Recent Comments