Software as a Service businesses are dependent on customer retention to maintain income. Companies naturally grow revenue faster if it continues to acquire and retain customers compared to just focusing on the existing customer base. Determining the rate of growth is therefore important to understanding the health of the SaaS platform. Hence, the Rule of 40.
Tutorial
AllCode’s tutorial articles deal with a particular area or technique of business or development, making it understandable to beginners or experts and concentrating on practical aspects of implementation.
Navigating AWS Complexity
Amazon’s Web Services is a very complex platform. Streamlining and optimizing production workflows can be challenging for inexperienced users. However, the benefit of learning grants options for better efficiency, reliability, security, and cost-effectiveness for operations run on AWS.
While complexity can be difficult to navigate, it’s not impossible. With the right level of expertise, AWS complexity can be navigated with ease.
Developing an AWS Multi-Account Strategy
There are several good strategic reasons for having multiple accounts tethered to a single AWS environment. For security, governance, and scalability purposes, it is ideal to have a number of accounts working together in an environment for the various employees to have access. Ideally, the following should be incorporated into the environment to make the most of what AWS can offer.
What is AWS Pinpoint?
Along with other marketing tools, AWS Pinpoint is a solution to better allow for multi-channel marketing. It is designed to work with current channels of communication and offers flexibility in its application. It is everything needed for campaigns, tracking customer interaction, and utilizing data to improve marketing efforts.
How the AWS Well-Architected Tool Improves Your Environment
The AWS Well-Architected Framework is a comprehensive set of standards that serve as best practices to enhance efficiency, stability, security, and resilience within the AWS platform. These standards are known to be quite challenging to meet, underscoring the importance of seeking assistance from third-party experts to conduct a thorough review of your infrastructure. Additionally, Amazon offers a range of tools to assist in validating that your environment aligns with these stringent standards. By adhering to the AWS Well-Architected Framework, businesses can ensure their cloud architecture is optimized for success and longevity.
Mistakes to Avoid with AWS Well-Architected Framework
Understandably, AWS does require a high amount of specialized knowledge to work with. It is a highly technical platform and cloud computing is still a relatively new field of work and study. It is incredibly easy to make mistakes from both a business perspective and a technical perspective and could result in falling short of operational goals, superfluous designs, poor optimization, and vulnerabilities.
AWS Well Architected Framework Best Practices
The AWS Well-Architected Framework is a set of guidelines that help users develop their environments in a way that’s reliable, secure, efficient, and cost-effective. It’s a complicated process, but there are several key objectives that developers can and should follow when constructing a project on the Amazon cloud. Having objectives to follow can help improve establishing those benchmarks.
GoDaddy to AWS Migration Guide
If you are looking for a useful guide on how to migrate your DNS from GoDaddy to AWS Route53, then you have come to the right place.
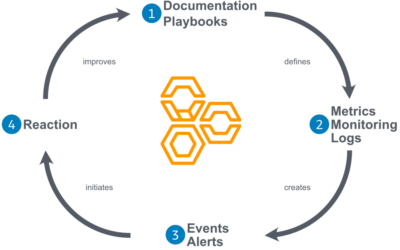
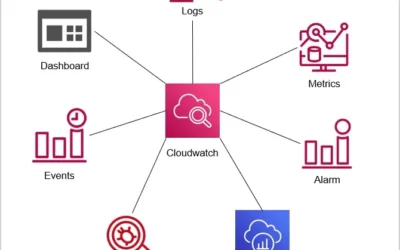
What is the Benefit of Centralized Log Management?
Most modern applications generate logs for all activities consisting of metadata regarding what was done. These provide crucial insight to the application’s health and can show when the system’s functionality has been compromised. Additionally, the data collected can provide knowledge on developing interests from application users. The main issue lies in the fact that an application can churn out thousands of logs over the course of its use which can easily prevent either of these bits of knowledge from seeing potential use. Hence the need for central log management.
Here’s Why You Should Work with an AWS Partner
Amazon Web Services is understandably a difficult platform to adapt to and utilize fully upon first getting started. Some organizations can be selected to become certified partners to indirectly extend services to help build on the Amazon Cloud. Finding a certified company to help build out is undoubtedly the best way to significantly simplify, streamline, and reduce the cost of utilizing AWS.