High control and governance is a large focal point of Amazon’s Cloud services. Another solid service for maintaining the wellbeing and compliance of any AWS service is Control Tower, helping to further simplify governance with enough room to integrate third-party software for scaling. AWS Control Tower main function is for the construction and monitoring of new AWS environments regardless of size and complexity.
Security
Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed.
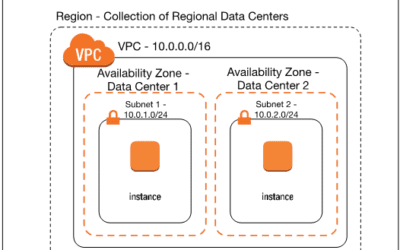
What is Wrong With my VPC Configuration?
The main purpose of the AWS Virtual Private Cloud is to keep any devices that want to avoid unauthorized access outside of public reach. Certain applications and top-priority data is kept explicitly within a confined network defined by the permissions the users set for the organization. However, there are a number of potential vulnerabilities that could occur that are all based on user-error and improper configuration of the VPC. AWS operates on shared responsibility and it’s partially down to the user to uphold their half.
10 AWS Security Tools to Implement in Your Environment
Amazon Web Services (AWS) scale very easily and securely with your application of choice. That’s not to say it is completely safe against intrusions. At least 70 percent of IT enterprise leaders are concerned about how secure the cloud is according to this report. As time progresses, there will be no end to those looking to exploit whatever loophole they can find in your security.
5 Tips for Creating a Strong Password
5 Tips for Creating a Strong Password Passwords protect the vulnerable information that makes up your life. Whether it be your bank information or social media account, behind the password lies personal details, which can be detrimental to your life if the wrong...
5 Tips to Stay Safe Online
5 Tips to Stay Safe Online Over the past decade, the fabric of daily life has become interwoven with smartphones, social media, and the apps that make rapid-fire technological innovations feel indispensable. These device-driven distractions create a blur of browsing...
Pareto Network’s ERC20 Smart Contract Audit Report
Pareto networks erc20 smart contract audit report 1. Introduction This document is a security audit of Pareto Network’s ERC-20 token contract supporting their decentralized ecosystem. The scope of the security audit was restricted to: Scan the contracts listed above...
Why Your ICO Needs KYC Compliance
Know Your Customer, referred to as ‘KYC’, is the process of knowing and identifying your customers. This is an integral piece of launching a token sale for Cryptocurrencies because of the regulations in certain countries like the United States, China, Korea and so on....
Successful Health Apps Part 2: User-Centered Design
Here is the second part of our blog series on building a successful healthcare application for web or mobile. This post focuses on utilizing ‘user-centered design’ methodologies to enhance the usability and usefulness of your app. But firstly, what is...
Technical Analysis of the $31 Million Dollar Ethereum Hack
Here's an interesting analysis of the $31 Million Ethereum Hack. http://medium.freecodecamp.org/a-hacker-stole-31m-of-ether-how-it-happened-and-what-it-means-for-ethereum-9e5dc29e33ce From a technical standpoint, it appears as though the software developers who built...
HIPAA Compliance in the Cloud
HIPAA Compliance for digital health startups is important. In this blog post, we'll define HIPAA, PHI, and HIPAA Compliance. We'll then provide practical examples of PHI. We will specify some steps that need to be taken to secure PHI in a cloud environment. We'll then...