What Makes a Well-Architected Framework?
These guidelines are meant to provide architects with consistent, easy-to-understand methods of evaluating a design. The concepts are defined as pillars and each covers a collection of concepts that developers need to consider as they construct their applications. It is critical to design an environment to be well architected and abides by these pillars as it will vastly simplify maintenance, reduce the cost of operation, maximize performance, and make the platform much more secure. The AWS well-architected pillars framework are as follows:
What Makes a Well-Architected Framework?
These guidelines are meant to provide architects with consistent, easy-to-understand methods of evaluating a design. The concepts are defined as pillars and each covers a collection of concepts that developers need to consider as they construct their applications. It is critical to design an environment to be well architected and abides by these pillars as it will vastly simplify maintenance, reduce the cost of operation, maximize performance, and make the platform much more secure. The pillars of a well-architected framework are as follows:
Operational Excellence
-
- The first goal is to clearly define operational objectives and goals. As basic as it may sound, this will dictate all the necessary services required in the final build.
- Make full use of the automated functions AWS has to automate processes that would otherwise require manual oversight. This will severely reduce the number of operations that could be subjected to human error.
- Continuously monitor and review for potential shortcomings. There could very likely be points that need further improvement and AWS services come with a variety of performance monitoring that could use improvement or cut costs.
- Encourage experimentation, innovation, and exploration of the AWS platform.
Security
AWS does have a complete complement of security services at their customers’ disposal to protect against potential threats. However, these security measures only cover half of what is required and will depend on the developers’ own abilities to keep security in mind.
-
- AWS Identity and Access Management (IAM) grants full control over user accounts and what permissions they have access to.
- Numerous services have data encryption as a feature and it should be applied when the application is both active and at rest.
- AWS Security Hub and AWS Config give a complete overview of an AWS environment and control over security compliance respectively.
- There are options to automate security testing and incident response processes in an environment.
Numerous services have data encryption as a feature and it should be applied when the application is both active and at rest. AWS Security Hub and AWS Config give a complete overview of an AWS environment and control over security compliance respectively. There are options to automate security testing and incident response processes in an environment. These tools not only enhance security but also reduce the need for continuous manual intervention, thereby minimizing the scope of privileged access and increasing overall security posture.
In the shared security responsibility model adopted by AWS, certain security obligations are divided between AWS and the user. AWS takes charge of securing the core infrastructure that supports all cloud services. This includes the physical security of data centers, the security of hardware, software, networking, and facilities, as well as ensuring the resilience of the global infrastructure. As a user, your responsibility encompasses securing the applications and data you run on AWS. By leveraging AWS, you effectively offload the responsibility of managing and maintaining physical hardware and foundational cloud software security, allowing you to focus more on your specific operational needs.
Operational Excellence
-
- The first goal is to clearly define operational objectives and goals. As basic as it may sound, this will dictate all the necessary services required in the final build.
- Make full use of the automated functions AWS has to automate processes that would otherwise require manual oversight. This will severely reduce the number of operations that could be subjected to human error.
- Continuously monitor and review for potential shortcomings. There could very likely be points that need further improvement and AWS services come with a variety of performance monitoring that could use improvement or cut costs.
- Encourage experimentation, innovation, and exploration of the AWS platform.
Security
AWS does have a complete complement of security services at their customers’ disposal to protect against potential threats. However, these security measures only cover half of what is required and will depend on the developers’ own abilities to keep security in mind.
-
- AWS Identity and Access Management (IAM) grants full control over user accounts and what permissions they have access to.
- Numerous services have data encryption as a feature and it should be applied when the application is both active and at rest.
- AWS Security Hub and AWS Config give a complete overview of an AWS environment and control over security compliance respectively.
- There are options to automate security testing and incident response processes in an environment.
Numerous services have data encryption as a feature and it should be applied when the application is both active and at rest. AWS Security Hub and AWS Config give a complete overview of an AWS environment and control over security compliance respectively. There are options to automate security testing and incident response processes in an environment. These tools not only enhance security but also reduce the need for continuous manual intervention, thereby minimizing the scope of privileged access and increasing overall security posture.
In the shared security responsibility model adopted by AWS, certain security obligations are divided between AWS and the user. AWS takes charge of securing the core infrastructure that supports all cloud services. This includes the physical security of data centers, the security of hardware, software, networking, and facilities, as well as ensuring the resilience of the global infrastructure. As a user, your responsibility encompasses securing the applications and data you run on AWS. By leveraging AWS, you effectively offload the responsibility of managing and maintaining physical hardware and foundational cloud software security, allowing you to focus more on your specific operational needs.
Reliability
Amazon’s cloud can alleviate numerous reliability threats over on-site infrastructure, but not all reliability issues. But while AWS instances can experience outages that are either natural or man-made, the cloud does have a number of redundancies and backups built-in with each AWS region.
-
- Each AWS region has a number of Availability Zones that can each hold its own instance of an application. Traffic can be controlled between all utilized Availability Zones and either towards desired instances or away from offline instances.
- AWS CloudFormation can be used to deploy, configure, and acquire resources. If need be, it can also gain access to third-party resources. Users can set up and automate backups and restore processes when they go offline.
- AWS CloudWatch will monitor applications and infrastructure for when errors and issues occur.
Reliability
Amazon’s cloud can alleviate numerous reliability threats over on-site infrastructure, but not all reliability issues. But while AWS instances can experience outages that are either natural or man-made, the cloud does have a number of redundancies and backups built-in with each AWS region.
-
- Each AWS region has a number of Availability Zones that can each hold its own instance of an application. Traffic can be controlled between all utilized Availability Zones and either towards desired instances or away from offline instances.
- AWS CloudFormation can be used to deploy, configure, and acquire resources. If need be, it can also gain access to third-party resources. Users can set up and automate backups and restore processes when they go offline.
- AWS CloudWatch will monitor applications and infrastructure for when errors and issues occur.
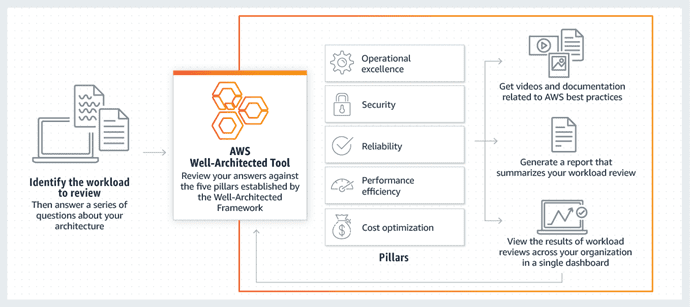
Performance and Efficiency
One of the bigger issues with more traditional cloud platforms is the risk of overprovisioning. Procure too few resources and the application will struggle to function in the wake of excess demand. Procure too many resources and while the application will run just fine, there’s an excessive number of instances that are unused and running their wheels, running up the monthly bill in the process. Ideally, the goal should be to optimize to minimize costs and maximize performance.
-
- Using AWS Auto Scaling can help direct traffic to specific instances based on demand.
- AWS Elastic Load Balancing and Amazon ElastiCache can distribute traffic evenly and improve application performance overall.
Cost Optimization
AWS can be a fairly cheap platform to use with its much more flexible pricing model. However, it can be esoteric at times and does require some degree of either exploration or second-hand expertise to refine.
-
- AWS Cost Explorer can monitor and analyze how AWS resources are spent.
- AWS Trusted Advisor will highlight opportunities to reduce costs and improve efficiency.
- Resources and services can be tagged to categorize and track.
- Understand what is being built and choose the right AWS pricing model.
Performance and Efficiency
One of the bigger issues with more traditional cloud platforms is the risk of overprovisioning. Procure too few resources and the application will struggle to function in the wake of excess demand. Procure too many resources and while the application will run just fine, there’s an excessive number of instances that are unused and running their wheels, running up the monthly bill in the process. Ideally, the goal should be to optimize to minimize costs and maximize performance.
-
- Using AWS Auto Scaling can help direct traffic to specific instances based on demand.
- AWS Elastic Load Balancing and Amazon ElastiCache can distribute traffic evenly and improve application performance overall.
Cost Optimization
AWS can be a fairly cheap platform to use with its much more flexible pricing model. However, it can be esoteric at times and does require some degree of either exploration or second-hand expertise to refine.
-
- AWS Cost Explorer can monitor and analyze how AWS resources are spent.
- AWS Trusted Advisor will highlight opportunities to reduce costs and improve efficiency.
- Resources and services can be tagged to categorize and track.
- Understand what is being built and choose the right AWS pricing model.
Finding Help Achieving These Standards
As a Select AWS partner, we have certified AWS experts who have worked on numerous projects in the past for various clients and intend on expanding on our existing experience. From helping build applications from the ground up to course-correcting half-finished applications, we have had an extensive history with the platform. If you need a helping hand to verify that your project meets AWS standards or even to reach that level of functionality in the first place, check out our offering on the AWS marketplace here.
Finding Help Achieving These Standards
As a Select AWS partner, we have certified AWS experts who have worked on numerous projects in the past for various clients and intend on expanding on our existing experience. From helping build applications from the ground up to course-correcting half-finished applications, we have had an extensive history with the platform. If you need a helping hand to verify that your project meets AWS standards or even to reach that level of functionality in the first place, check out our offering on the AWS marketplace here.
