Cybersecurity is a constant concern. In the ever-evolving landscape of cybersecurity, threats are becoming increasingly sophisticated and must be constantly met to protect our increasingly interwoven infrastructure. As a result, Generative AI emerges as a potential transformative force in enhancing cybersecurity measures, focusing on threat detection, anomaly detection, and the generation of robust security protocols to fortify the security posture of applications and systems.
Security
Allcode protects our clients online with industry-leading security. Everything we make is protected with powerful built-in security technologies that help detect and block threats before there is a problem.
Maintaining IoT Devices with Generative AI
In the intricate network of the Internet of Things (IoT), where devices are the silent orchestrators of seamless connectivity, the introduction of Generative AI heralds a new era in predictive maintenance. However, with how isolated IoT devices can be, it’s important to maintain vigilance and a cautious eye on what needs to be fixed and what still works. With the right application and execution, Generative AI’s capacity for predicting and preventing potential malfunctions makes it a reliable tool and significantly helps significantly reduce maintenance downtime.
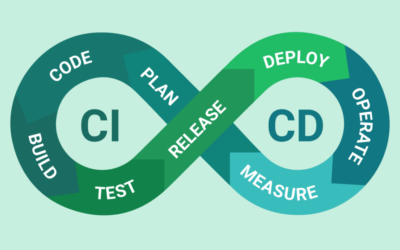
Top 5 CI/CD Automation Frameworks
CI/CD pipelines are the means by which development teams continuously deliver and integrate applications. It is a strenuous process that requires iterations and constant adjustments before rolling out updates. The time to deploy can be shortened significantly through the use of automated testing and provisioning.
AWS Well Architected Framework Remediation
Ideally, optimization of an AWS environment should be a one-and-done task, but there are plenty of risk factors to consider and sufficient room to forget. High risk issues (HRIs) are architectural and operational decisions that could very easily negatively impact how a business works. Even with in-house help with the automated assistant tools, it is best practice to have manual third-party help to best optimize for individual needs and requirements the business may have.
Best Practices for Using AWS Systems Manager
As newer users adopt the AWS cloud, it can be difficult to watch for issues and resolve them as needed. AWS Systems Manager grants better visibility over the AWS environment by clustering resources, providing legible and usable data based on performance, and actions to take that abide by AWS compliance requirements and best practices. This service provides everything management needs to evaluate the cloud and ensure continued functionality.
How the AWS Well-Architected Tool Improves Your Environment
The AWS Well-Architected Framework is a comprehensive set of standards that serve as best practices to enhance efficiency, stability, security, and resilience within the AWS platform. These standards are known to be quite challenging to meet, underscoring the importance of seeking assistance from third-party experts to conduct a thorough review of your infrastructure. Additionally, Amazon offers a range of tools to assist in validating that your environment aligns with these stringent standards. By adhering to the AWS Well-Architected Framework, businesses can ensure their cloud architecture is optimized for success and longevity.
AWS Financial Services
While the Amazon Cloud at large is meant to be flexible in how it is applied, there are a number of services that are more directly tailored to specific industries. The financial industry for example has solutions set out to help them merge their usual operations with the benefits cloud technology can provide. It has provided many companies with the capability to adapt to new regulations and further optimize their existing services.While the Amazon Cloud at large is meant to be flexible in how it is applied, there are a number of services that are more directly tailored to specific industries. The financial industry for example has solutions set out to help them merge their usual operations with the benefits cloud technology can provide. It has provided many companies with the capability to adapt to new regulations and further optimize their existing services.
How to Setup AWS Control Tower in Your Environment
High control and governance is a large focal point of Amazon’s Cloud services. Another solid service for maintaining the wellbeing and compliance of any AWS service is Control Tower, helping to further simplify governance with enough room to integrate third-party software for scaling. AWS Control Tower main function is for the construction and monitoring of new AWS environments regardless of size and complexity.
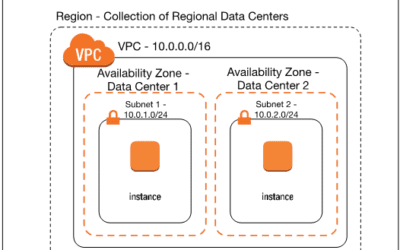
What is Wrong With my VPC Configuration?
The main purpose of the AWS Virtual Private Cloud is to keep any devices that want to avoid unauthorized access outside of public reach. Certain applications and top-priority data is kept explicitly within a confined network defined by the permissions the users set for the organization. However, there are a number of potential vulnerabilities that could occur that are all based on user-error and improper configuration of the VPC. AWS operates on shared responsibility and it’s partially down to the user to uphold their half.
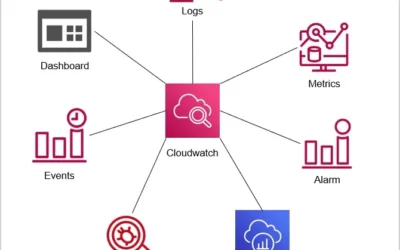
What is the Benefit of Centralized Log Management?
Most modern applications generate logs for all activities consisting of metadata regarding what was done. These provide crucial insight to the application’s health and can show when the system’s functionality has been compromised. Additionally, the data collected can provide knowledge on developing interests from application users. The main issue lies in the fact that an application can churn out thousands of logs over the course of its use which can easily prevent either of these bits of knowledge from seeing potential use. Hence the need for central log management.