Data lakes are repositories for structured or unstructured data of any capacity or type. With the tools available from AWS, data does not necessarily need to be organized first before running a number of analytics, visualization, or machine learning processes to yield the most optimal results.
Data security
Data security means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach.
What is Wrong With my VPC Configuration?
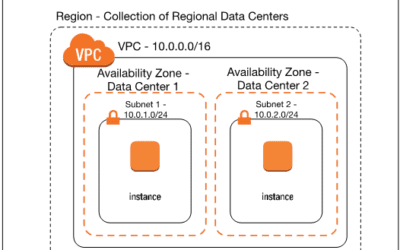
The main purpose of the AWS Virtual Private Cloud is to keep any devices that want to avoid unauthorized access outside of public reach. Certain applications and top-priority data is kept explicitly within a confined network defined by the permissions the users set for the organization. However, there are a number of potential vulnerabilities that could occur that are all based on user-error and improper configuration of the VPC. AWS operates on shared responsibility and it’s partially down to the user to uphold their half.
Top 5 Data Security Threats to Healthcare
Top 5 Data Security Threats to Healthcare Every aspect of daily life has been permeated by technological progress: the “traditional” way of doing things, from even a generation ago, is now rendered obsolete and antiquated by the digital revolution. Accordingly, the...
5 Tips to Stay Safe Online
5 Tips to Stay Safe Online Over the past decade, the fabric of daily life has become interwoven with smartphones, social media, and the apps that make rapid-fire technological innovations feel indispensable. These device-driven distractions create a blur of browsing...