Building on the Amazon cloud can be complicated as it does require an extensive amount of knowledge beforehand on how to work with many of the services. AWS IQ is a marketplace where experts can sell their expertise and users can put out requests for specific cloud needs. Along with putting out a task, parties can then discuss terms of payment, scope of the project, scheduling, and project requirements.
Cloud
Cloud development involves, is where Allcode shines. Our AWS certified engineers develop cloud architecture such as planning, organizing, and designing to implementing and structuring cloud delivery models (Iaas, Paas, Iaas).
Managed Container Apps Effortlessly with AWS App Runner
Amazon also supports the construction of web applications among other types of projects and solutions on their platform. Even with less experience, users are given a reliable platform for running containers or applications securely and at scale. AWS App Runner is capable of adjusting to the needs of the application whether it be compliance, the scale it needs to operate at, and latency.
How to Setup AWS Control Tower in Your Environment
High control and governance is a large focal point of Amazon’s Cloud services. Another solid service for maintaining the wellbeing and compliance of any AWS service is Control Tower, helping to further simplify governance with enough room to integrate third-party software for scaling. AWS Control Tower main function is for the construction and monitoring of new AWS environments regardless of size and complexity.
What is AWS Glue and Why are Pipelines Important?
The most important components of a service are the service itself and the sources of its data, but those parts are completely worthless if they are separate and without the necessary connective tissue between them. AWS Glue is a serverless data pipeline that assists in finding data sources, preparing those sources, and directing data accordingly to where it’s needed. It’s easy to use and supports multiple processing and workload types.
What is Wrong With my VPC Configuration?
The main purpose of the AWS Virtual Private Cloud is to keep any devices that want to avoid unauthorized access outside of public reach. Certain applications and top-priority data is kept explicitly within a confined network defined by the permissions the users set for the organization. However, there are a number of potential vulnerabilities that could occur that are all based on user-error and improper configuration of the VPC. AWS operates on shared responsibility and it’s partially down to the user to uphold their half.
AWS Storage Options – Should I Use S3, EFS, or EBS?
While incorporating the use of physical storage databases into Amazon’s Web Services is an option, there are also cloud storage options available. There are a few options to choose with significant differences between each in order to tackle certain options. One of the following services will be better optimized for handling loads at scale while another will have a better time retaining a proper load balance.
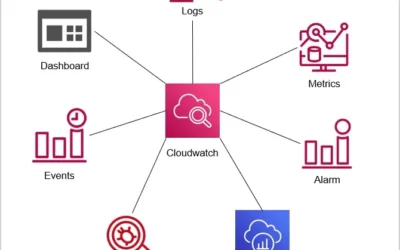
What is the Benefit of Centralized Log Management?
Most modern applications generate logs for all activities consisting of metadata regarding what was done. These provide crucial insight to the application’s health and can show when the system’s functionality has been compromised. Additionally, the data collected can provide knowledge on developing interests from application users. The main issue lies in the fact that an application can churn out thousands of logs over the course of its use which can easily prevent either of these bits of knowledge from seeing potential use. Hence the need for central log management.
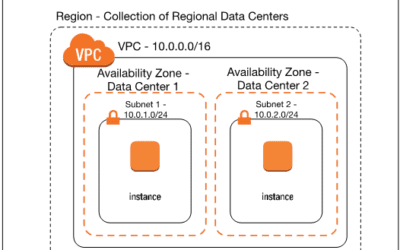
AWS Virtual Private Cloud
If whatever is being launched on AWS needs to be private, the Virtual Private Cloud (VPC) provides enough functionality for such a task. It grants full control over the virtual network environment from resource allocation to security and is simple to start up. There are options for choosing the IP range, creating subnets, and configuring route tables. The only connections to this network are completely user-defined.
What to Do When AWS Goes Offline?
Amazon’s services are not completely iron-clad and applications built on the platform are still vulnerable to the occasional hiccup. When it does happen, there is a degree of shared responsibility between AWS and the developers of the web applications. All services are designed with redundancies in mind and much of the physical infrastructure does come with backup databases and availability zones to help cover for any instances that go down or are brought down for maintenance. Though data loss is mitigated, it is still advisable to prepare for the next incident.
5 Types of Cybersecurity You Will Need
Cybercrime is a perpetually evolving threat that demands the most out of companies’ ability to adapt in turn. There are a variety of threats present that can damage a company in a variety of ways from siphoning critical information off to unwanted third parties to damaging company equipment or putting information behind a paywall. Even for those who aren’t security specialists, having a basic grasp of these concepts is important to have.