Cybercrime is a perpetually evolving threat that demands the most out of companies’ ability to adapt in turn. There are a variety of threats present that can damage a company in a variety of ways from siphoning critical information off to unwanted third parties to damaging company equipment or putting information behind a paywall. Even for those who aren’t security specialists, having a basic grasp of these concepts is important to have.
Security
Allcode protects our clients online with industry-leading security. Everything we make is protected with powerful built-in security technologies that help detect and block threats before there is a problem.
Microsoft Azure vs. Alibaba Cloud
Microsoft and Google may be some of the biggest names struggling to overtake Amazon’s dominance of the cloud service market, but they aren’t the only names. Since 2009, Alibaba has had its own cloud computing platform with ventures into ecommerce data mining and processing and currently stands as the fifth largest company in artificial intelligence development. For now, we’ll be comparing Alibaba with some of its more immediate competition to put things into proper perspective.
Building Networks as a Service with Secure Gateways
Networks as a Service (NaaS) are network services that are rented out over the cloud. This can save organizations on funding and resources that would otherwise have gone towards maintaining infrastructure and lets them put all the requirements for maintenance out of house. All that said, there are more than enough ways any data coming in or out of the cloud can be compromised. These are some critical tools that could help in the construction of NaaS.
AWS Web Application Firewall
If your web apps or APIs are at risk of being hacked or compromised by bots, AWS Web Application Firewall (WAF) is a virtual firewall that can assist defend you from these threats. AWS WAF gives you comprehensive control over traffic accessing your applications by allowing you to set security rules that restrict bot traffic and stop classic attack types like SQL injection and cross-site scripting. Additionally, you have the option of creating rules that only allow certain types of traffic.
Top 5 Reasons Why Cybersecurity is a Good Investment
The popularity of cloud computing and mobile devices is revealing many opportunities for cyberattacks. In this article, learn why your organization should invest in cybersecurity and how you can get started.
Top 5 Data Security Threats to Healthcare
Top 5 Data Security Threats to Healthcare Every aspect of daily life has been permeated by technological progress: the “traditional” way of doing things, from even a generation ago, is now rendered obsolete and antiquated by the digital revolution. Accordingly, the...
5 Tips for Creating a Strong Password
5 Tips for Creating a Strong Password Passwords protect the vulnerable information that makes up your life. Whether it be your bank information or social media account, behind the password lies personal details, which can be detrimental to your life if the wrong...
5 Tips to Stay Safe Online
5 Tips to Stay Safe Online Over the past decade, the fabric of daily life has become interwoven with smartphones, social media, and the apps that make rapid-fire technological innovations feel indispensable. These device-driven distractions create a blur of browsing...
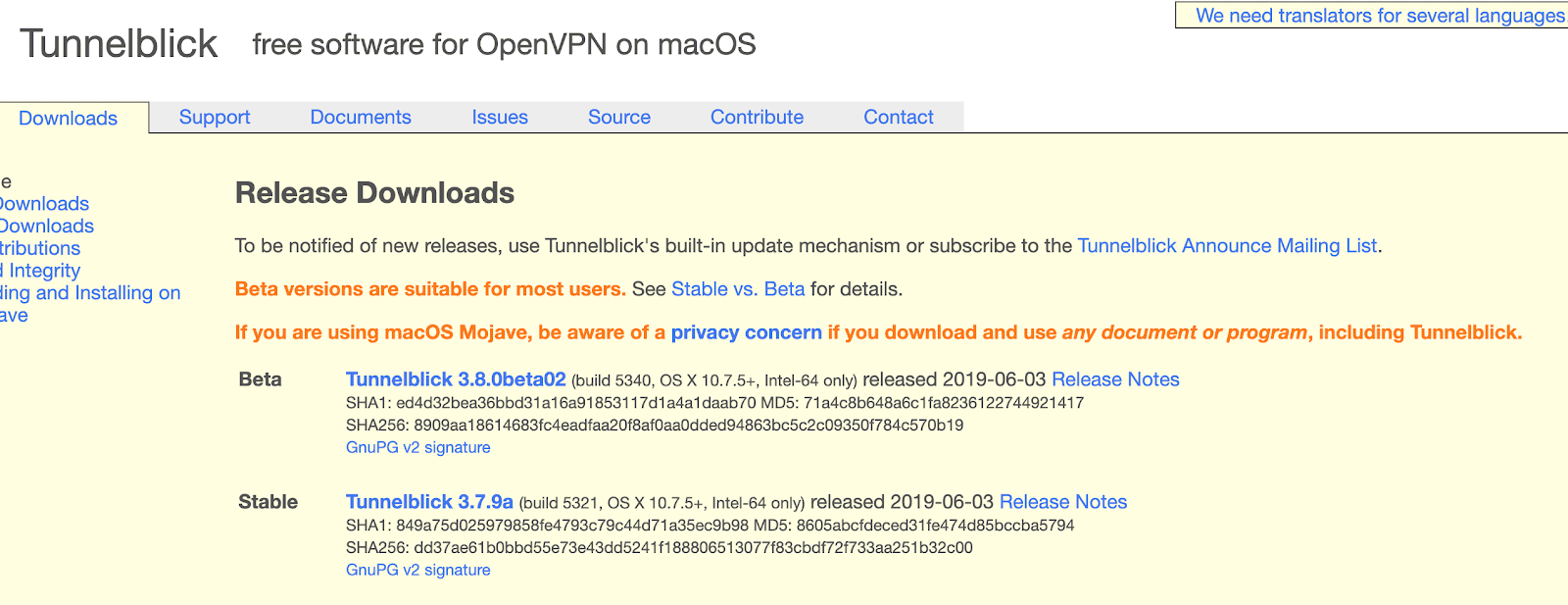
How to connect to a VPN on Mac OS X with OpenVPN, Tunnelblick, and DUO
How to connect to a VPN on Mac OS X with OpenVPN, Tunnelblick, and DUO Download Tunnelblick. - http://tunnelblick.net/downloads.html (stable version is advised) Install Tunnelblick.Launch TunnelblickDrop the opvn configuration file provided by your system...
Pareto Network’s ERC20 Smart Contract Audit Report
Pareto networks erc20 smart contract audit report 1. Introduction This document is a security audit of Pareto Network’s ERC-20 token contract supporting their decentralized ecosystem. The scope of the security audit was restricted to: Scan the contracts listed above...