Cybersecurity is a constant concern. In the ever-evolving landscape of cybersecurity, threats are becoming increasingly sophisticated and must be constantly met to protect our increasingly interwoven infrastructure. As a result, Generative AI emerges as a potential transformative force in enhancing cybersecurity measures, focusing on threat detection, anomaly detection, and the generation of robust security protocols to fortify the security posture of applications and systems.
Cybersecurity
Computer security, cybersecurity or information technology security is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
AllCode is an AWS Public Sector Partner
Globally, various AWS partnered companies such as ourselves are lending their services to public sector organizations to overcome and circumnavigate a variety of technical challenges with the cloud. Through the Public Sector Partnership Program, Amazon aims to boost their partners’ visibility to government entities and improve engagement overall. Both partner and public sector organizations alike can hope to benefit through this program through improved marketing materials and streamline operations respectively.
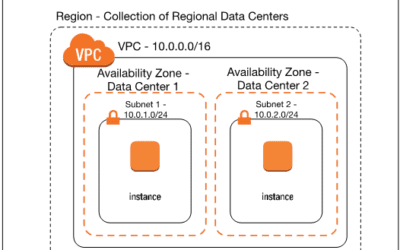
What is Wrong With my VPC Configuration?
The main purpose of the AWS Virtual Private Cloud is to keep any devices that want to avoid unauthorized access outside of public reach. Certain applications and top-priority data is kept explicitly within a confined network defined by the permissions the users set for the organization. However, there are a number of potential vulnerabilities that could occur that are all based on user-error and improper configuration of the VPC. AWS operates on shared responsibility and it’s partially down to the user to uphold their half.
Top 15 DeFi Crypto Coins and DApps (2024 Edition)
In this article, we highlight 15 of our top DeFi picks for 2024. By the end of this article, you will understand the basics of DeFi, some of the top projects, and how to get in on the action.
How to farm MATIC on SushiSwap
Amazon Textract is a great tool that enables healthcare facilities to quickly and easily gather data in raw forms, such as healthcare claims, medical charts, and more.
5 Tips to Stay Safe Online
5 Tips to Stay Safe Online Over the past decade, the fabric of daily life has become interwoven with smartphones, social media, and the apps that make rapid-fire technological innovations feel indispensable. These device-driven distractions create a blur of browsing...
"How Do I Raise Investment?" Advice for Healthcare Startups
Hi Healthcare Startup Innovators! We are scheduling our next Meetup for June 22nd in Arent Fox LLP, Downtown SF. The evening will kick-off at 6pm with snacks and networking, with the event proper starting at 6:30 / 6:40pm and run until 8pm. Of course you are welcome...